About FenixPyre
About FenixPyre
About FenixPyre
Elegant Innovation for
Data Security
Elegant Innovation for Data Security
At FenixPyre, we’re redefining how organizations protect what matters most - their data.
In a world where cyber threats are more sophisticated, insider risks more subtle, and data more mobile than ever, traditional DLP isn’t enough. That’s why we built FenixPyre: a PADS platform that safeguards sensitive information no matter where it travels, who accesses it, or how it’s shared.
Our mission is simple - make enterprise-grade data protection effortless, intelligent, and scalable. From ransomware prevention to insider threat mitigation and third-party risk control, we help businesses take back control of their data with solutions that are as powerful as they are easy to deploy.
Rooted in innovation and designed for today’s hybrid, cloud-first world, FenixPyre enables organizations to move fast, stay compliant, and operate with confidence - without ever compromising on security.
Whether you’re securing an enterprise or a growing startup, FenixPyre helps you protect every file, everywhere - instantly.
At FenixPyre, we’re redefining how organizations protect what matters most - their data.
In a world where cyber threats are more sophisticated, insider risks more subtle, and data more mobile than ever, traditional DLP isn’t enough. That’s why we built FenixPyre: a PADS platform that safeguards sensitive information no matter where it travels, who accesses it, or how it’s shared.
Our mission is simple - make enterprise-grade data protection effortless, intelligent, and scalable. From ransomware prevention to insider threat mitigation and third-party risk control, we help businesses take back control of their data with solutions that are as powerful as they are easy to deploy.
Rooted in innovation and designed for today’s hybrid, cloud-first world, FenixPyre enables organizations to move fast, stay compliant, and operate with confidence - without ever compromising on security.
Whether you’re securing an enterprise or a growing startup, FenixPyre helps you protect every file, everywhere - instantly.
At FenixPyre, we’re redefining how organizations protect what matters most - their data.
In a world where cyber threats are more sophisticated, insider risks more subtle, and data more mobile than ever, traditional DLP isn’t enough. That’s why we built FenixPyre: a PADS platform that safeguards sensitive information no matter where it travels, who accesses it, or how it’s shared.
Our mission is simple - make enterprise-grade data protection effortless, intelligent, and scalable. From ransomware prevention to insider threat mitigation and third-party risk control, we help businesses take back control of their data with solutions that are as powerful as they are easy to deploy.
Rooted in innovation and designed for today’s hybrid, cloud-first world, FenixPyre enables organizations to move fast, stay compliant, and operate with confidence - without ever compromising on security.
Whether you’re securing an enterprise or a growing startup, FenixPyre helps you protect every file, everywhere - instantly.
Meet our leadership team.
Our
Vision
Our Vision
At FenixPyre, our vision is to create a digital world where data remains secure, intelligent, and in control - no matter where it goes.
We believe the future of cybersecurity lies in protecting information at its source: the data. As organizations embrace cloud, mobility, and distributed collaboration, traditional perimeter-based defenses fall short. FenixPyre envisions a paradigm shift—one where security follows the data, adapting in real time and empowering teams to operate freely without sacrificing protection.
We’re not just building security tools - we’re shaping the next generation of resilient digital infrastructure, one secure file at a time.
At FenixPyre, our vision is to create a digital world where data remains secure, intelligent, and in control - no matter where it goes.
We believe the future of cybersecurity lies in protecting information at its source: the data. As organizations embrace cloud, mobility, and distributed collaboration, traditional perimeter-based defenses fall short. FenixPyre envisions a paradigm shift—one where security follows the data, adapting in real time and empowering teams to operate freely without sacrificing protection.
We’re not just building security tools - we’re shaping the next generation of resilient digital infrastructure, one secure file at a time.
At FenixPyre, our mission is to protect what matters most - your data-wherever it lives, moves, or is shared.
We are building a future where sensitive data is safeguarded at the file level - regardless of where it travels, who accesses it, or how it’s shared. Our platform empowers organizations to prevent ransomware, neutralize insider threats, and enforce third-party governance, all without disrupting productivity.
Designed for simplicity, performance, and adaptability, FenixPyre addresses the escalating demands of data protection with a solution that’s cloud-native, frictionless, and built for growth. We’re not just securing information - we’re enabling digital trust at scale.
At FenixPyre, our mission is to protect what matters most - your data-wherever it lives, moves, or is shared.
We are building a future where sensitive data is safeguarded at the file level - regardless of where it travels, who accesses it, or how it’s shared. Our platform empowers organizations to prevent ransomware, neutralize insider threats, and enforce third-party governance, all without disrupting productivity.
Designed for simplicity, performance, and adaptability, FenixPyre addresses the escalating demands of data protection with a solution that’s cloud-native, frictionless, and built for growth. We’re not just securing information - we’re enabling digital trust at scale.
Our
Mission
Our Mission
Our
Values
Our Values
Quality
We are committed to providing excellent data security software for our customers, so that data is never leaked.
We are committed to providing excellent data security software for our customers, so that data is never leaked.
We are committed to providing excellent data security software for our customers, so that data is never leaked.
Innovation
We believe technology is a force for good, that can help make our lives easier. That’s why we are dedicated to creating meaningful products that allow organizations to achieve their full potential.
Simplicity
We are dedicated to providing easy-to-use solutions so that data security is never a hassle.
We are dedicated to providing easy-to-use solutions so that data security is never a hassle.
We are dedicated to providing easy-to-use solutions so that data security is never a hassle.
Continuous Learning
We strive to learn new things every day. We believe that learning continues outside of the classroom.
We strive to learn new things every day. We believe that learning continues outside of the classroom.
We strive to learn new things every day. We believe that learning continues outside of the classroom.
50+ Patent Claims
Millions of files protected
50+ Patent Claims
Millions of files protected
50+ Patent Claims
Millions of files protected
Award Winning
Platform
Award Winning
Platform

Cybersecurity Excellence Award
Cybersecurity Excellence Award

CRN Tech Innovator Finalist, Zero Trust Security
CRN Tech Innovator Finalist, Zero Trust Security

Finalist MIT Sloan CIO Summit
Finalist MIT Sloan CIO Summit

USAF ABMS
USAF ABMS

USAF ABMS
Latest News
Explore The FenixPyre
Data Security Platform

See how
FenixPyre supports your
Data Governance program

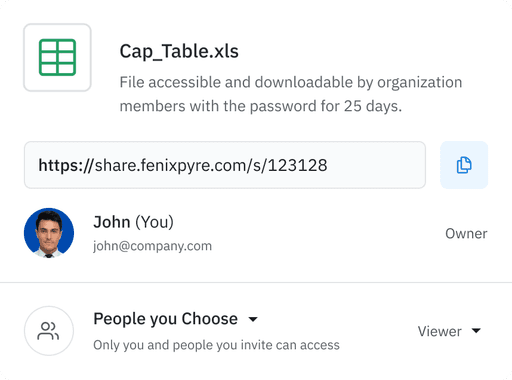
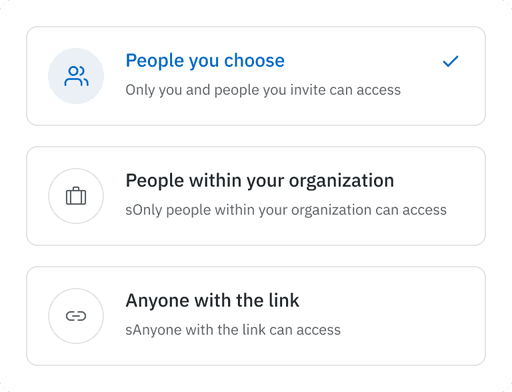
See how FenixPyre supports your Data Governance program

See how FenixPyre supports your
Data Governance program

solutions

© 2018-2026 FenixPyre Inc, All rights reserved

solutions
7775 Walton Parkway
Suite 224
New Albany, OH 43054

© 2018-2026 FenixPyre Inc, All rights reserved

solutions
7775 Walton Parkway
Suite 224
New Albany, OH 43054

© 2018-2026 FenixPyre Inc, All rights reserved