Post-Authentication Data Security Platform
Core Features
Seamless User Experience
Post-Authentication Data Security
File Type Agnostic

Secure External Sharing
Share encrypted files securely with external partners while maintaining full control over access. Permissions can be revoked instantly without retrieving or reissuing files.

Rapid Onboarding
Deploy FenixPyre in days, not months, with lightweight agents installed in minutes. Encrypt data at scale — up to 1TB every six hours — and configure policies within hours.

Incremental Rollout
Start with a single department and expand at your own pace. FenixPyre enables a land-and-expand model without requiring enterprise-wide rollout upfront.

Identity Provider Integration
Integrates seamlessly with Azure AD, Okta, Google Workspace, and other enterprise identity providers. Leverage your existing authentication infrastructure for streamlined and secure access control.

Central Policy Automation & Management
Define, automate, and enforce encryption and access policies from a single centralized console. Gain full visibility into how your data is accessed and used across environments.

Patented Dynamic Access Controls
Enforce role-based and location-aware access policies with instant revocation capability. Files remain encrypted and protected even if copied, stolen, or exfiltrated.

Layered AES-256 Key Management
Each file is encrypted with a unique AES-256 File Encryption Key (FEK), which is then encrypted by a Customer Master Key. Files and keys are stored separately to ensure multi-layered, zero-knowledge protection.

Strong & Performant Key Security
All File Encryption Keys are stored in a high-performance database and can only be decrypted within a secure Hardware Security Module (HSM). File contents remain cryptographically inaccessible to anyone outside the authorized access list.

Bring Your Own Master Key (BYOK)
Maintain full ownership and control by bringing your own Customer Master Key (CMK/CMEK). Keys can be stored and managed within the Hardware Security Module of your choice.

Comprehensive Key Backups
Encryption keys are automatically backed up with hourly, 6-hour, daily, weekly, monthly, and yearly snapshots. Backups are securely stored across multiple U.S. regions for maximum durability and disaster recovery.

Real-Time Monitoring & Analytics
Integrates directly with SIEM platforms to provide live audit logs, behavioral analytics, and anomaly detection. Monitor access patterns in real time and respond proactively to potential threats.

Infinite Scale
Built to support billions of encryption keys and the largest enterprise environments without performance degradation. FenixPyre scales seamlessly as your data footprint and organizational complexity grow.

Ultra-Low Latency Performance
Encryption and decryption are optimized through a robust client and SaaS architecture with kernel-level efficiencies. File access adds as little as ~100 milliseconds of latency, delivering a near-native user experience.

Multi-Region Redundancy
FenixPyre SaaS is deployed across multiple U.S. regions to ensure high availability and automatic failover. Your encryption infrastructure remains resilient and operational even during regional disruptions.

Seamless Offboarding
Offboard FenixPyre at any time without vendor dependency or operational disruption. Customers retain full access to their encryption keys and can decrypt data using our secure offboarding utility.

24/7 Enterprise Support
Our global support team is available around the clock to ensure uninterrupted operations. Enterprise customers receive responsive, expert assistance whenever needed.
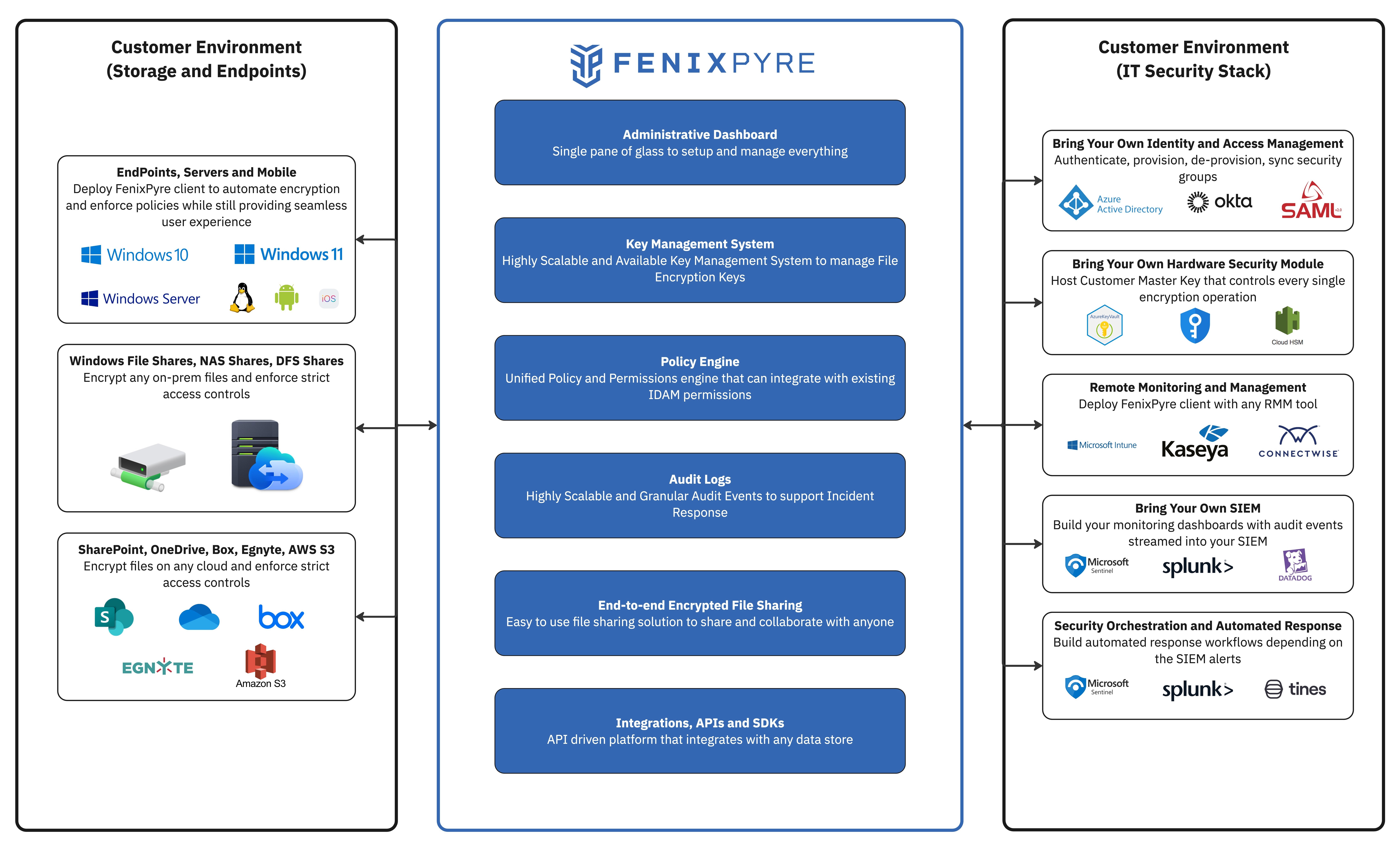
Implementing FenixPyre in Three Steps
FenixPyre integrates with your existing IT stack and complements your current security architecture.